Secunia PSI is a must for any Windows machines
Keeping up with program patches and updates can be extremely difficult, but thanks to your friends over at Secunia, those problems can be all but eliminated! This is a (somewhat) complete guide on getting Secunia PSI (Personal Software Inspector), installing, and running it! This program is a must for anyone who runs any Windows OS. This is partly because it’s only available for Windows. These images were taken from a Windows 7 Home Premium 64-bit OS, but it should be pretty much the same for any other OS.
At the time of this writing Secunia PSI was on version 1.5.0.2.
First, lets get Secunia PSI downloaded. Head on over to Secuina.com and look for the download button.
After downloading head over to where ever you saved it to, and double-click to run. NOTE: Windows may ask is you want to run the program, click yes!
Now follow the instructions. Images below will help guide you through the process.
Select a language.
Click Next

I accept the terms of the License Agreement (Don’t forget to read it!)
Select Personal Use, unless you are using it for business purposes.
More reading
Tell it where to install
Once done, click finish
It will ask if you want to run it. Say yes.
Once it starts you may see message saying “Please wait while network connectivity is verified.” Have no fear, this is normal. As soon as the program can see the servers it will continue. If you have a software firewall installed you may need to allow Secunia PSI access to the Internet.
Now onto usage!
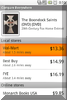
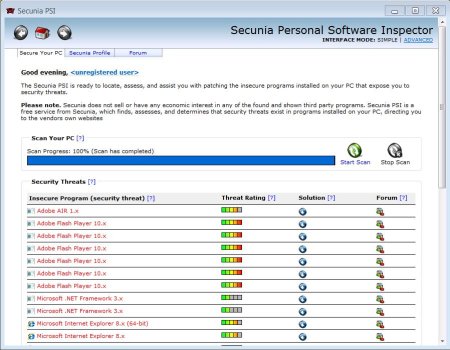
After the program scans it will come up with a list like this. This image is a good scenario (of a bad situation), you may get one just like it or worse. If the insecure program is listed as a Microsoft product it should be dealt with by using Windows Update. I did not include how to do this because it varies from XP, Vista, and 7.
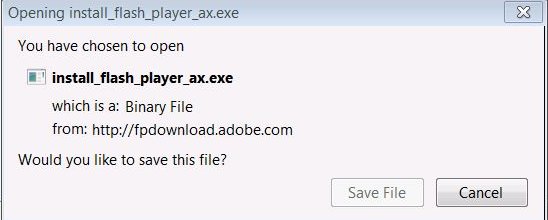
Here I’m going to update Adobe Flash Player 10.x. I click on the Blue down arrow, I get a dialog box to download the new software.
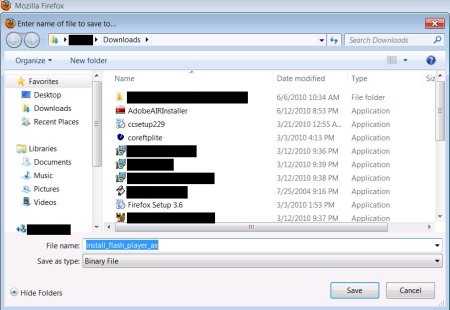
Save the file (remember where you save it to!)
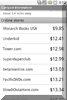
Then run it! Just follow the steps for each program. In this case there were many listings for Adobe Flash Player. You only need to download it once and run it once. Once you scan again it will show them all fixed up. (FYI: The reason it lists many copies is because Flash Player is installed in several places due to different web browsers)
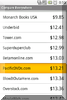
After you do this a few times and run windows update you can manually start the scan again. Once you are set you will see something like this.
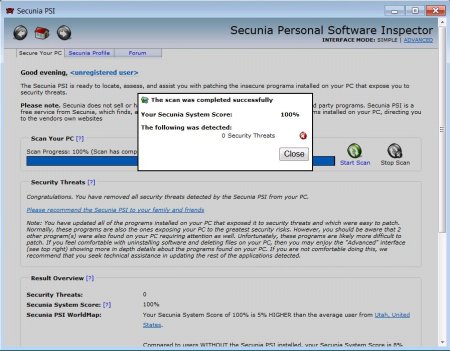
You are set! Look at you! You have already mastered this awesome utility!
By default Secunia PSI is set to run at system startup. This may not be best if you are on a laptop, or have a very slow computer. If Secunia PSI is running you will see a little icon in the bottom left corner of your screen. It looks a little like this.

Questions?