Using SSH as a secure proxy
Recently I started school (which is why I haven’t done much of anything on my sites) where they have a wifi connection just like at a coffee shop. The problem with these open networks is that people (like myself) can run a packet catcher like WireShark and get user names and password for various sites such as yahoo, facebook, and myspace. Since when you log in to those you are doing so without https (encryption). Also my school logs every site to visit and when I’m bored in class I don’t want them to know I’m researching hacking sites.
To solve this I setup a Linux box on my network and point port 22 to it. 22 is the default SSH port in case you didn’t know. Then I create a secure tunnel from my laptop to my home box (my laptop also running Linux).
SSH -D 1080 username@ip
This creates what is essentially a SOCKS v5 proxy on port 1080. Anything and everything you do remotely can be routed through 1080 (any port works, I just like that number).
Now I don’t know how to setup my Linux machine so that I don’t need to configure every program I use to work with the proxy and currently have to setup everything manually. Here is how to do it with FireFox.
Open FireFox, goto Edit –> Preferences –> Advanced –> Network –> Connection –> Settings
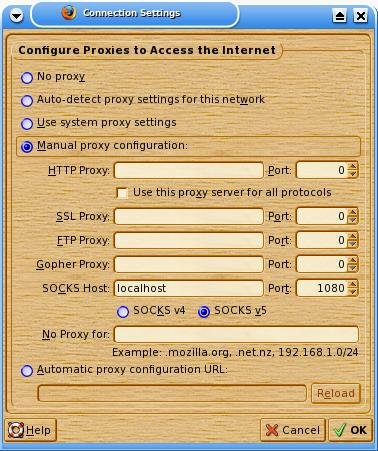
Click “Manual proxy configuration:”, then under SOCKS Host put “localhost” port “1080” and make sure that SOCKS v5 is clicked.
Where it says “No Proxy For” you can leave localhost in, I’m not really sure, never tried. I just cleared it out and everything went smoothly.
Close the window and start surfing!
As long as you keep the SSH connection alive this will work. If you SSH connection does die you will know right away when you can’t surf. You will also need to revert your connection settings back when you are no longer using the SSH proxy. Also keep in mind that even tho you are routing via an encrypted tunnel to your remote machine, traffic will still be unencrypted after that point. Surfing may take longer than you would like. This is due to the fact that ALL traffic will be routed first to your remote machine then to you via the tunnel.
Lastly, I’m told that not every SSHd configuration allows SSH proxies. Mine does. I’m not sure why, I haven’t bothered to look into that yet. You may need to check your /etc/sshd_config file as there may be an option there. If you need help you know where to ask for it. Enjoy!
I recently came across your blog and have been reading along. I thought I would leave my first comment. I don’t know what to say except that I have enjoyed reading. Nice blog. I will keep visiting this blog very often.
Susan
http://8080proxy.com
NEW INFO! I found out that even tho your traffic is encrypted through the SSH tunnel your DNS queries aren’t! To fix this goto the address bar and type “about:config”. This may give you a message saying to be careful, say ok then in the search bar type “network.proxy.socks_remote_dns” and change it’s value to “True”. Now all your DNS queries are done through the proxy! Thanks to Hak5 for the tip!